Preliminary Program
Notice that technical programs, reception, and banquet will be held in different places! See the venue page or the guidebook for more information.
February 26
17:00 Opening
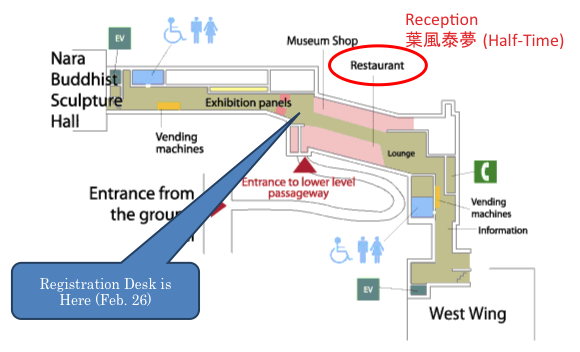
17:00–20:00 Registration (at Nara National Museum)
You can visit Buddhist Sculpture Hall in Nara National Museum (reserved by PKC) until 18:00.
18:00–20:00 Reception (Restaurant “葉風泰夢 (Half-Time)” located in Nara National Museum)
Notice the registration desk is still open during the reception.
February 27
8:40– Registration (at the Nara Prefectural New Public Hall)
In Feb. 27th–Mar. 1st, the registration desk is in Nara Prefectural New Public Hall. Do not go to Nara National Museum!
9:10–9:25 Opening
9:25–10:40 Encryption (Session Chair: Masayuki Abe)
- Key Encapsulation Mechanisms from Extractable Hash Proof Systems, Revisited
- Takahiro Matsuda (AIST, Japan)
- Goichiro Hanaoka (AIST, Japan)
- Robust Encryption, Revisited
- Pooya Farshim (Darmstadt University of Technology, Germany)
- Benoit Libert (Technicolor, France)
- Kenneth G. Paterson (Royal Holloway, University of London, UK)
- Elizabeth A. Quaglia (ENS, France)
- Sender Equivocable Encryption Schemes Secure against Chosen-Ciphertext Attacks Revisited
- Zhengan Huang (Shanghai Jiao Tong University, China)
- Shengli Liu (Shanghai Jiao Tong University, China)
- Baodong Qin (Shanghai Jiao Tong University, China and Southwest University of Science and Technology, China)
10:40–11:00 Coffee Break
11:00–12:00 Invited Talk (Session Chair: Tatsuaki Okamoto)
- Functional Encryption: Origins and Recent Developments
- Brent Waters (University of Texas at Austin, USA)
12:00–14:00 Lunch (Yume-Kaze Plaza)
14:00–15:40 Primitives (Session Chair: Claudio Orlandi)
- Feasibility and Infeasibility of Adaptively Secure Fully Homomorphic Encryption (#1)
- Jonathan Katz (University of Maryland, USA)
- Aishwarya Thiruvengadam (University of Maryland, USA)
- Hong-Sheng Zhou (University of Maryland, USA)
- Efficient, Adaptively Secure, and Composable Oblivious Transfer with a Single, Global CRS
- Seung Geol Choi (Columbia University)
- Jonathan Katz (University of Maryland)
- Hoeteck Wee (George Washington University)
- Hong-Sheng Zhou (University of Maryland)
- Cryptography Using CAPTCHA Puzzles
- Abishek Kumarasubramanian (UCLA, USA)
- Rafail Ostrovsky (UCLA, USA)
- Omkant Pandey (The University of Texas at Austin, USA)
- Akshay Wadia (UCLA, USA)
- Improved Zero-knowledge Proofs of Knowledge for the ISIS Problem, and Applications
- San Ling (Nanyang Technological University, Singapore)
- Khoa Nguyen (Nanyang Technological University, Singapore)
- Damien Stehle (ENS, Lyon, France)
- Huaxiong Wang (Nanyang Technological University, Singapore)
15:40–16:00 Coffee Break
16:00–17:15 Functional Encryption/Signatures (Session Chair: Mehdi Tibouchi)
- Decentralized Attribute-Based Signatures
- Tatsuaki Okamoto (NTT, Japan)
- Katsuyuki Takashima (Mitsubishi Electric, Japan)
- On the Semantic Security of Functional Encryption Schemes
- Manuel Barbosa (HASLab - INESC TEC and Universidade do Minho, Portugal)
- Pooya Farshim (Darmstadt University of Technology, Germany)
- Attribute-Based Encryption with Fast Decryption
- Susan Hohenberger (Johns Hopkins University, USA)
- Brent Waters (University of Texas at Austin, USA)
February 28
9:00–9:50 On RSA (Session Chair: Steven Galbraith)
- Recovering RSA Secret Keys from Noisy Key Bits with Erasures and Errors
- Noboru Kunihiro (The University of Tokyo, Japan)
- Naoyuki Shinohara (NICT, Japan)
- Tetsuya Izu (Fujitsu Laboratories, Japan)
- Combined Attack on CRT-RSA -- Why Public Verification Must Not Be Public
- Guillaume Barbu (Oberthur Technologies, France)
- Alberto Battistello (Oberthur Technologies, France)
- Guillaume Dabosville (Oberthur Technologies, France)
- Christophe Giraud (Oberthur Technologies, France)
- Guénaël Renault (Université Paris 6 / LIP6, France)
- Soline Renner (Oberthur Technologies and Université Bordeaux 1 / IMB, France)
- Rina Zeitoun (Oberthur Technologies and Université Paris 6 / LIP6, France)
9:50–10:40 IBE and IPE (Session Chair: Katsuyuki Takashima)
- Revocable Identity-Based Encryption Revisited: Security Model and Construction
- Jae Hong Seo (NICT, Japan)
- Keita Emura (NICT, Japan)
- Improved (Hierarchical) Inner-Product Encryption from Lattices
- Keita Xagawa (NTT, Japan)
10:40–11:00 Coffee Break
11:00–12:00 Invited Talk (Session Chair: Kaoru Kurosawa)
- Techniques for Efficient Secure Computation Based on Yao's Protocol
- Yehuda Lindell (Bar-Ilan University, Israel)
12:00–14:00 Lunch (Yume-Kaze Plaza)
14:00–18:00 Excursion (Bus Tour to Horyuji Temple)
We meet at 14:00 at Nara Prefectural New Public Hall (the conference venue). After the tour the buses will go to the banquet venue. If you don't attend the tour, go directly to Nara Hotel for the banquet. See the venue page for location information.
18:00–21:00 Banquet (Nara Hotel)
March 1
9:00–9:50 Key Exchange (Session Chair: Shai Halevi)
- Non-Interactive Key Exchange
- Eduarda S.V. Freire (Royal Holloway, University of London, UK)
- Dennis Hofheinz (Karlsruhe Institute of Technology, Germany)
- Eike Kiltz (Ruhr-Universität Bochum, Germany)
- Kenneth G. Paterson (Royal Holloway, University of London, UK)
- Efficient UC-Secure Authenticated Key-Exchange for Algebraic Languages
- Fabrice Ben Hamouda (ENS, Paris, France)
- Olivier Blazy (Ruhr-Universität Bochum, Germany)
- Céline Chevalier (University of Paris II, France)
- David Pointcheval (ENS, Paris, France)
- Damien Vergnaud (ENS, Paris, France)
9:50–10:40 Signature Schemes I (Session Chair: Benoît Libert)
- Tighter Reductions for Forward-Secure Signature Schemes
- Michel Abdalla (ENS, Paris, France)
- Fabrice Ben Hamouda (ENS, Paris, France)
- David Pointcheval (ENS, Paris, France)
- Tagged One-Time Signatures: Tight Security and Optimal Tag Size
- Masayuki Abe (NTT, Japan)
- Bernardo David (University of Brasilia, Brazil)
- Markulf Kohlweiss (Microsoft Research, USA)
- Ryo Nishimaki (NTT, Japan)
- Miyako Ohkubo (NICT, Japan)
10:40–11:00 Coffee Break
11:00–12:15 Homomorphic Encryption (Session Chair: Ludovic Perret)
- Packed Ciphertexts in LWE-based Homomorphic Encryption
- Zvika Brakerski (Stanford University, USA)
- Craig Gentry (IBM Research, USA)
- Shai Halevi (IBM Research, USA)
- Vector Commitments and their Applications (#2)
- Dario Catalano (Università di Catania, Italy)
- Dario Fiore (MPI-SWS, Germany)
- Chosen Ciphertext Secure Keyed-Homomorphic Public-Key Encryption
- Keita Emura (NICT, Japan)
- Goichiro Hanaoka (AIST, Japan)
- Go Ohtake (Japan Broadcasting Corporation, Japan)
- Takahiro Matsuda (AIST, Japan)
- Shota Yamada (The University of Tokyo, Japan)
12:15–14:00 Lunch (Yume-Kaze Plaza)
14:00–15:40 Signature Schemes II (Session Chair: Noboru Kunihiro)
- Efficient Completely Context-Hiding Quotable and Linearly Homomorphic Signatures
- Nuttapong Attrapadung (AIST, Japan)
- Benoit Libert (Technicolor, France)
- Thomas Peters (Universite catholique de Louvain, Belgium)
- Verifiably Encrypted Signatures with Short Keys based on the Decisional Linear Problem and Obfuscation for Encrypted VES
- Ryo Nishimaki (NTT, Japan)
- Keita Xagawa (NTT, Japan)
- Sequential Aggregate Signatures with Short Public Keys: Design, Analysis and Implementation Studies
- Kwangsu Lee (Columbia University, USA)
- Dong Hoon Lee (Korea University, Korea)
- Moti Yung (Google Inc. and Columbia University, USA)
- New Constructions and Applications of Trapdoor DDH Groups
- Yannick Seurin (ANSSI, Paris, France)
15:40–16:00 Coffee Break
16:00–17:15 Protocols (Session Chair: Eiichiro Fujisaki)
- Rate-Limited Secure Function Evaluation
- Özgür Dagdelen (Technische Universität Darmstadt, Germany)
- Payman Mohassel (University of Calgary, Canada)
- Daniele Venturi (Aarhus University, Denmark)
- Verifiable Elections That Scale for Free
- Melissa Chase (MSR Redmond, USA)
- Markulf Kohlweiss (MSR Cambridge, USA)
- Anna Lysyanskaya (Brown University, USA)
- Sarah Meiklejohn (UC San Diego, USA)
- On the Connection between Leakage Tolerance and Adaptive Security
- Jesper Buus Nielsen (Aarhus University, Denmark)
- Daniele Venturi (Aarhus University, Denmark)
- Angela Zottarel (Aarhus University, Denmark)
17:15–17:30 Closing
#1 and #2 have been switched.


